IT might be difficult to imagine that anyone would willing attack healthcare systems, and yet these are becoming a popular target for cybercriminals. Throughout the COVID-19 epidemic, the healthcare industry has seen an explosion of cyber-attacks. According to the World Economic Forum, the CyberPeace Institute analyzed data from over 235 attacks (excluding data breaches) all targeting the healthcare industry across 33 countries.
While this represents a small portion of the total number of such attacks, it serves as a powerful indicator of a rising negative trend. Regardless of size, healthcare institutions must prepare for heightened frequency cyber-attacks by preparing their staff and cyber defenses to resist threat actors.
Let Stefanini serve as your cybersecurity partner. Visit our Solution page to learn more.
Impact of Cyber-Attacks on Healthcare
Led by hacking and IT incidents, The healthcare sector saw a record 45.67M patient records exposed in data breaches in 2021 largest annual total since 2015 (scmagazine). Healthcare institutions are an obvious target for cybercriminals because they hold large stores of sensitive patient data, all of which represent significant monetary and intelligence value in the wrong hands.
Protected health information (PHI) of patients, financial information such as credit card and bank account numbers, personally identifying information (PII) such as Social Security numbers, and intellectual property relating to medical research and innovation are among the data sets targeted. On the dark web, stolen health records may sell for up to ten times the price of stolen credit card numbers.
In today’s computerized environment, cybersecurity in healthcare and data protection are vital for enterprises and critical infrastructure to function normally. Highly confidential ePHI (electronic protected health information) are managed in various computerized operating systems by practically every clinic and hospital.
Likewise, EHRs (electronic health records) systems practice management support systems, clinical decision support systems, and computerized physician order entry systems are just a few of the examples of specialized hospital information systems used by many healthcare companies that in turn serve at cyber-attack targets. Further, as medical systems rely more on the myriad of devices that comprise the Internet of Things (IoT), safeguarding each device represents a mounting challenge.
While enabling quick access to patient or network data, the scale of these systems cause health care institutions to become particularly vulnerable targets for cyberattacks. Even worse, the cost of repairing a breach in the department of health is nearly three times that of other industries, averaging $408 per stolen health care record against $148 each stolen health care record.
The first step in defending your organization from cyber risks is understanding the sort of attacks that hackers can perform:
- Phishing: Computer systems are infected with malware after clicking on links or attachments in phishing emails, social media posts, or text messages.
- MITM (Man-in-the-Middle) attacks: Cybercriminals intrude into conversations or data transfers to steal confidential (and extremely valuable) user information, resulting in significant losses and fines.
- Attacks on network vulnerabilities: ARP cache poisoning, HTTPS spoofing, and other cybercrimes target medical centers’ most important asset: their wired and wireless networks, which give access to patient data.
- Ransomware Attacks: Criminals not only encrypt data and demand money to decrypt it, but they also restrict access to the entire clinical system, thus paralyzing the work of surgical and life-support equipment.
Benefits of Cyber Security in Healthcare
For the sake of both medical staff and patients, hospital cybersecurity must improve. Robust cybersecurity protocols can produce various tangible benefits for health and human services. Here are some examples:
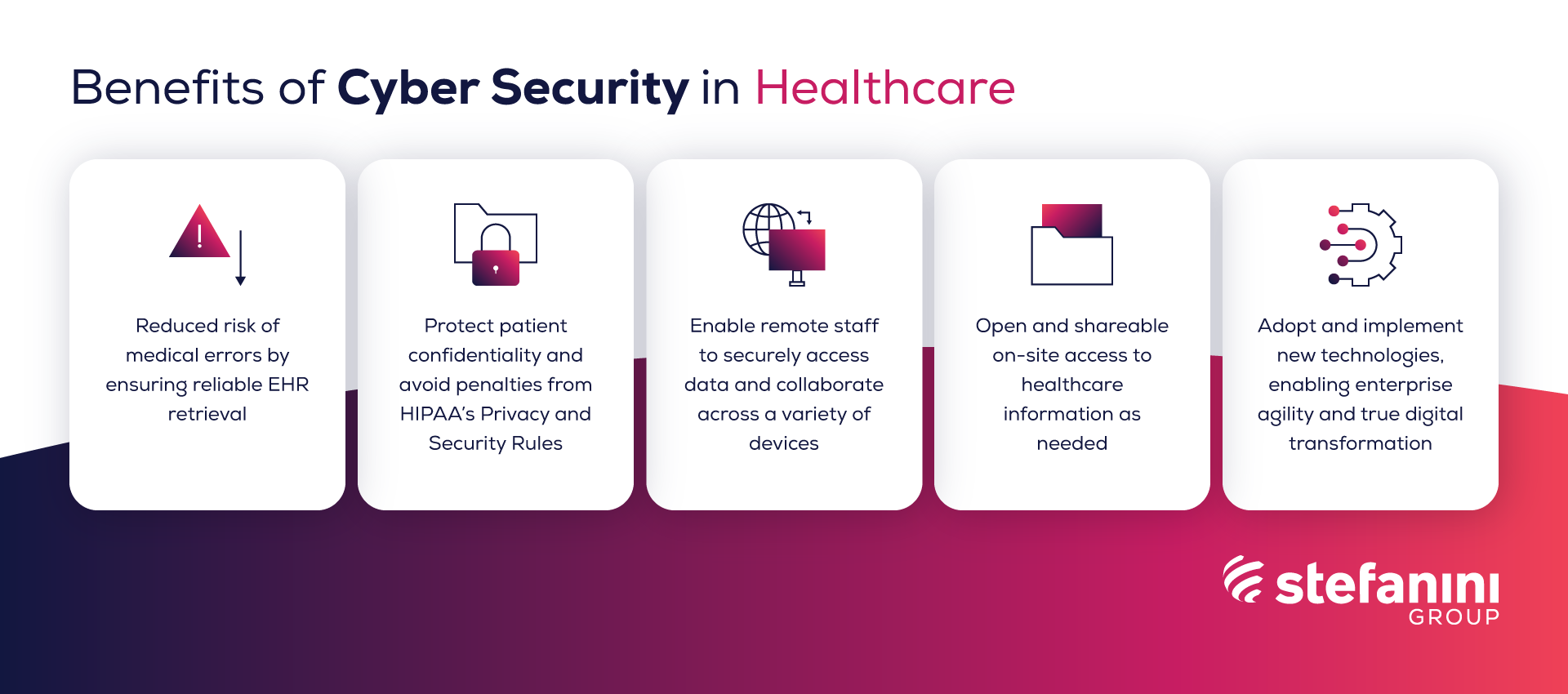
- Reduced Risk of Medical Errors: Medical errors would be more likely if EHRs were not accessible quickly and reliably. Because doctors and nurses don’t have a complete picture of a patient’s data, they may mistakenly provide an ineffective or even hazardous treatment. EHRs would be safer and these errors would be avoided if cybersecurity was improved.
Protecting patient confidentiality: Because hackers have access to PHI and other sensitive information, cyberattacks on electronic health records and other systems constitute a risk to patient privacy. Your business could risk significant penalties under HIPAA’s Privacy and Security Rules, as well as potential harm to its reputation in the community, if it fails to maintain the privacy of patient, covered entities and business records. - Remote Access: Staff need to access data remotely, opening up more opportunities for attack – In the healthcare business, collaboration is critical, with departments working together to deliver the best answer for each patient. Those who require information aren’t always at their desks; they frequently operate remotely from various devices.
- Open and Shareable healthcare information: On-site and remote access to confidential patient data is required, as well as access across many devices. The high level of urgency in the medical profession needs a team’s capacity to communicate information swiftly.
- Secure Tech Adoption: The healthcare sector does not slow down making it difficult to effectively implement new systems or technology. The added concern of keeping new implementations secure makes adoption even more challenging. However, a robust cybersecurity strategy can ensure that businesses can effectively and securely implement new technologies, enabling enterprise agility and true digital transformation.
Transform healthcare with these top 5 IoT integrations. Click here to learn more!
How to Prevent Cyber-attacks on Health Information Systems
The best defense starts with recognizing cyber risk as a business and strategic risk management issue. The following are some key actions your organization to create better cybersecurity measures.
- Personnel development: According to an IONOS Cloud research, 40% of employees lack cybersecurity experience or data protection awareness. As a result, professional and ongoing cybersecurity training is critical:
- Use good digital hygiene measures, such as creating strong passwords and avoiding clicking on unexpected or questionable sites.
- Backup data: Employees must create backups on a regular basis with rigorous data encryption measures since cyberattacks can harm and remove valuable patient information.
- Recognize phishing emails, especially ones meant for specific recipients. Personnel should be trained on how to recognize suspicious messages, make efforts to communicate with other employees if their name is being used in suspicious messages, and report such instances.
In addition to standardized training, your organization should consider dedicating at least one full-time position to leading the information security program. This function should be given high priority so that he or she has enough authority, status, and independence to be effective. Additionally, security personnel should receive regular risk assessment updates, as well as descriptions of what measures are being implemented to dynamically reduce the continuously changing cyber risk.
- Data Usage Management: Clinics should keep track of harmful file activity and keep an eye on it. They can do so by putting in place mechanisms that restrict illegal data access, prevent the distribution of unauthorized emails, and limit the capacity to copy to external sources, among other things:
- Keep track of data and monitor unauthorized access to patient files. In the event of a cyberattack, logs will assist a clinic in quickly identifying and eliminating the breach.
- Encrypt data during transmission and storage using modern cryptography. Homomorphic encryption, secure multiparty computation, and distributed ledger technologies are all possibilities.
- Leverage cloud storage and multi-factor authentication to ensure the secure verification of employee credentials
- Monitor Mobile and Connected Devices: For doctors and administrative staff the use of mobile phones, applications, and devices have become common practice. However, there is another troubling weakness. Hackers steal information, passwords, and smartphones, as well as hacking, eavesdropping, and reconfiguring connected equipment. The following are strategies that can prevent such breaches:
- Create a separate network for IoT devices, monitor them for rapid changes in activity levels, and disable actions that are unnecessary.
- Protect lost or stolen phones with multi-factor authentication, application data encryption, and remote lockout.
- Update software, such as safety programs and medical sensor control systems, on a regular basis.
Finally, the most critical protection is to develop a cybersecurity culture that prioritizes patient safety. This enables health-care businesses to supplement their existing patient-centered culture with a cybersecurity-focused culture. A cybersecurity culture in which employees see themselves as proactive defenders of patients and their data will have a significant impact on the organization and patients’ cyber risk.
Address digital equity across your healthcare initiatives. Click here to get started.
Protect Healthcare Information Systems with Stefanini
The digitization of healthcare systems enables better outcomes. Yet, the complexity and variety of these information networks and the devices that access them make it challenging to keep your network secure.
Stefanini offers a proactive cybersecurity strategy that provides 24/7 monitoring, as well as offensive and defense strategies to stop breaches before they occur.
No matter the scale of your enterprise, we can help you achieve a robust security posture that resists cyber-attacks.
Contact us and speak with an expert today!




















