Lackadaisical attitudes toward physical and cybersecurity in our critical infrastructure are needlessly placing our society in harm’s way.
To rob banks, you must really want what’s inside. As a prospective robber, you’ve got to be very good at several different skills; disguises, welding, locksmithing, gun violence, explosives, get-away driving, and perhaps tunneling. Or gamble with the ‘ole high risk, low reward, Hollywood standard of just walking into the lobby and handing a note to the teller. Sometimes that works, depending on the bank.
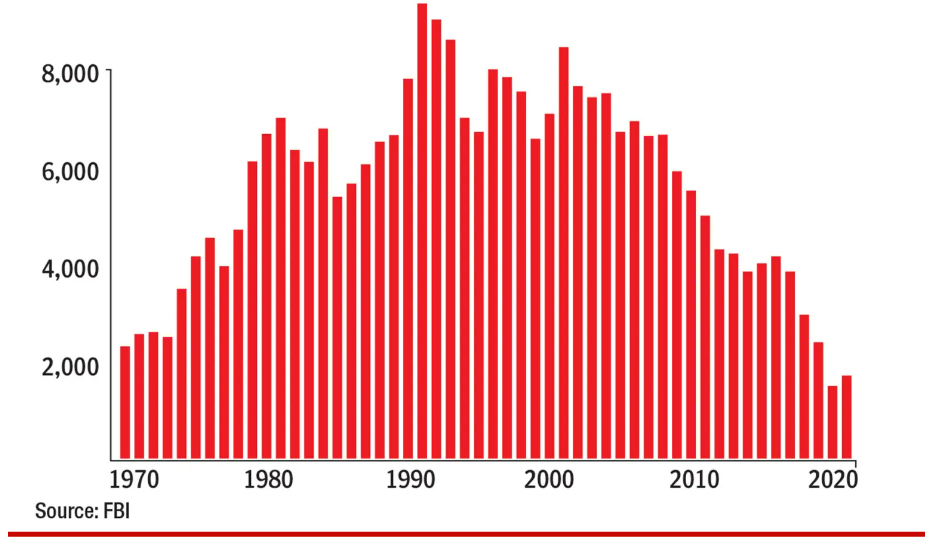
Statistics show that if robbers can physically get the money out of the bank, chances are about 80% that they’ll get away with it – but getting out of the bank is tricky these days. Banks have stepped up their game and deployed multiple layers of defense against bank robbery. The 2021 FBI statistics on bank robbery security devices are as follows:
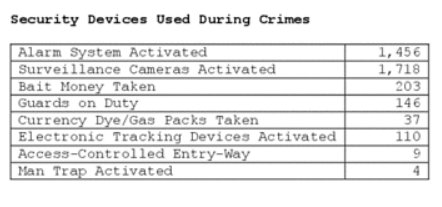
Any one of these devices can stop a bank robbery career before it starts, but perhaps the most effective security is the physical bank itself. The vault is designed to keep money in, and the bank lobby is designed to keep would-be robbers OUT during off hours, but IN during bank hours.
To get away with their spoils, modern bank robbers must make it through the gauntlet of the Access Control Vestibule aka the “Bullet Proof Man Trap”. The Access Control Vestibule is essentially a cage that the robber needs to exit through, and if the teller, from behind their own bullet-proof glass window, hits the alarm, then the vestibule becomes an instant waiting room for the federal penitentiary.
The robber sits inside, enjoying a floor to ceiling view, until the police arrive and extract the loot, the handgun, and the mask, from a built-in surrender hatch, while the security system emails forensics videos and timeline logs straight to the police station. The Man Trap automates everything on this side of a 10-to-25-year prison sentence, except a last shower.
Applying simple diligence to the realm of bank security is the reason why the number of bank robberies is dropping to new all-time lows. In the U.S., the average bank robbery nets $4,800 – not even enough to buy a get-away car. Would-be robbers are thinking twice.
Bank Robberies
Shut the front door
Installing a man trap in your lobby doesn’t mean the bank is safe, but it does mean that your bank probably won’t be robbed by someone just walking in the front door. Such is not the case, however, for much of our critical infrastructure. Even though we value our critical infrastructure, we haven’t yet been willing to invest in man trap style defense systems to protect it. Consequently, much of our critical infrastructure is susceptible to being robbed, vandalized, or destroyed by bad actors simply walking through the front door.
Not only is it free from man-trap scale defenses, but critical infrastructure is also vulnerable to more than just robbery. Critical infrastructure saboteurs are motivated by far more than money: anger, politics, revenge, misunderstanding, and mental illness. In our culture today, there are many groups that just want to harm society at large, and vandalizing or destroying a system that the rest of us depend on is seen as an acceptable way to satisfy their appetite for retribution.
There are relatively few people who would brave a man trap to rob a bank, but many more folks might give it a try if all that stood between them, and piles of cash, was a screen door latched with a simple hook. That is largely the state of our critical infrastructure defenses today: screen door latch and a sign.
Outside of airports, which were only recently upgraded to “Man Trap” style cybersecurity, much of our critical infrastructure is just sitting out in the open, with nothing more than a token amount of security.
Far too often, that “security” amounts to a brightly colored sign, warning the perpetrator not to proceed or they may suffer incarceration or cause severe damage to the system.
Signage like this is useless, at least as a deterrent. It’s something the lawyers have informed us, must be in place, but it won’t stop crime or protect our infrastructure. Warning signs are useless, ugly, and can actually be helpful to the criminal: the following sign is easily read by a criminal as “Reminder: don’t forget to disconnect the alarm system before you open this door.”
There are vastly superior paradigms for keeping our critical Infrastructure secure, such as “Security by Obscurity”. That is, keep the infrastructure “out of sight” so it stays “out of mind”. This is a legitimate and often cost-effective security technique.
It would be irresponsible of me to give specific examples of how a low skilled, highly motivated person could cause massive damage to one or more of our critical infrastructures. I’ll save that for the “White Hat Attack” I’ll be paid to conduct later to prove my point. It’ll suffice to say, our critical systems are wide open and easy to take down.
Just look for yourself:

Check out this electrical sub-station, which supplies power to a large neighborhood. See how it is enclosed by a chain-link fence? Does this look very secure? Seems to me this is about the same level of protection given to a private tennis court. Ironically, I’m fairly certain the fence is not electrified. Nor do I think the sub-station has video surveillance or motion detectors. Like many of them, this substation is out in the open for everyone to see, or isolated on a side road where no one can see it but it’s still easy to access, where you could probably pitch a tent without anyone noticing and camp out while plotting your attack, maybe even with time to tunnel in. Why bother though, when you can merely tin snip through that non-electrified chain-link when no one is looking (which is all the time).
I’m thinking 5 minutes? Maybe under 1 minute if you practiced, and you’ve cut a hole big enough for a truck with full tank of gas to pass through. Not particularly clever, but a devastatingly effective way to put a neighborhood in the dark, not to mention the time it would take to repair.
A critical asset like this electrical substation should not be accompanied by the cheapest security options imaginable. If we invest the amount of money in infrastructure that matches its value to our society, then we could easily afford a secure building that blends into the environment, is “concealed” by landscaping, with reactive security systems, designed and sited with a higher level of integration into the environment, and that serves a useful dual purpose such as a charging station. Some expense, yes, but how much do you value your toasted bread each morning? Your air conditioning? What about hospital respirators?
Think of the ubiquitous fiber optics pedestal which supplies communications (Internet, Phone, TV) to neighborhoods. These pedestals can be found all over and are necessary for the distribution of fiber optics and copper communications, generally considered essential for modern life and business.
Yes, it’s sealed shut and you need a special tool to get it open – that or a single blow from a hammer, and then a couple more whacks to destroy the connections inside.
Really, you don’t even need to get out of your car, you could just run them over and destroy dozens in a single day.
Did I already say, “wide open”? A good rule of thumb is that if your security systems can be breached unintentionally by a drunk person, then they’re not very good security systems.
These fiber optic pedestals should be locked in underground manholes, blast proof, flood proof, teenager proof, and since we love and depend on our critical infrastructure so much, there should be landscaping and shrubbery abounding, perhaps an illuminated kiosk with a USB charger: useful and beautiful; instead of cheap and exposed.
Not spending now means paying later
This isn’t about comfort. Many of the services that are necessary for us to live are based on IT and need to be protected. You might be fine without being able to book a trash pickup with your city’s sanitation department but the backend system that scheduled those pickups may be on the same network that enables 911 dispatch or the Fire Department GPS system.
There have been hundreds of publicly reported cyber-attacks against hospitals and schools in 2023. Recently, hospitals in Texas, New Jersey, New Mexico, and Oklahoma were forced to divert ambulances from their emergency rooms and cancel elective procedures due to a ransomware attack.
Banks have largely stepped it up on cyber-crime and invested in the virtual version of a man trap, but cities, utilities, telecom, food, hospitals, and manufacturing are not ready for an attack by teenage hackers, or a disgruntled employee, much less a serious nation state attack.
Yes, it’s going to cost us, but not spending now means we will pay later.
Talk to the Texans who lost their electricity and water for weeks in 2022, because of unregulated utilities that didn’t factor the freezing temperature of water into their resiliency systems. Texans were reduced to a near stone-age existence, for no good reason. The US has always been susceptible to this unwillingness to invest in our own society, but this dangerous shortsightedness needs to end, or we will continue to suffer.
A similar level of un-preparedness exists when it comes to cyber threats to our critical infrastructure. We could prevent many of the physical and cyber vulnerabilities, but we have not gotten serious on a national scale.
The current presidential administration is finally addressing the issue at a federal level and has launched the Cybersecurity Maturity Model Compliance (CMMC) initiative, setting the standard for cyber maturity, and requiring all companies in the federal supply chain to pass a cybersecurity audit that verifies multiple layers of cybersecurity have been implemented. The hope is that these federal mandates will roll out into the commercial space.
Securing critical infrastructure requires a clear understanding of how important our critical infrastructure is, how vulnerable it is, and how to best protect it. Only when our society decides that we can no longer tolerate interruptions to our basic services will we truly make our infrastructure a resilient, convenient, even beautiful, part of our surroundings. The bottom-line approach to designing our society needs to factor in the staggering expense of critical infrastructure disruptions.
Fortunately, there are so many synergies between security and function.
Critical infrastructure protections can be part of the design of our society, including the physical design: think infrastructure meets public art. There is strong precedent for disguising cell phone towers as trees, blending telecom huts into structures, planting shrubbery and flowers around electrical distribution stations, and several other forms of accommodating and protecting our critical infrastructure while at the same time adding to the integrity and beauty of our communities.
When it comes to wreaking havoc on our critical infrastructure, a determined individual armed with nothing more than a 5 lb. hammer, a hack saw, some blueprints, and a Kia Sedona can bring a city to its knees.
Simple and effective deterrents are available but often not implemented for short-sighted ideological reasons. We can protect ourselves and our critical infrastructure, but we must commit to it.
We need to decide, as a society, what we value more: a handful of oligarchs who, no matter what happens, will always be able to afford to protect themselves – or our basic services and the American way of life.