Cloud services have been a recurring theme on the agenda of CIOs, technology executives, infrastructure and systems directors or managers for at least 7 years, with cloud adoption viewed as relevant for most IT services where there is a focus on Software as a Service (SaaS) solutions. Meanwhile, for application modernization, we have seen projects being accelerated by deployments based on Platform as a Service (PaaS) and low-code platforms. There has also been a huge acceleration as a result of the flexibility offered by Infrastructure as a Service (IaaS), which is particularly relevant in situations where existing on-premises deployments are reused, or when there is a lift-and-shift strategy for a quick exit from proprietary or colocation datacenters.
It’s worth taking a step further to properly explore these IaaS, PaaS and SaaS strategies. How do public cloud providers structure their infrastructure to enable possibilities at scale? How do businesses ensure their security within cloud environments with such a varied horizon? This article will focus on define and connect most of these concepts.
The image below offers a visual representation of a transition to the cloud involving the adoption of IaaS, PaaS and SaaS strategies. These three acronyms are related to the level of responsibility that is transferred to the cloud provider, enabling the business to focus instead on data and application functionality. Notably, these layers and accountability may vary on a case-by-case basis, but this strategy will determine potential efficiencies and outcomes in terms of converting CAPEX from IT resources to OPEX.
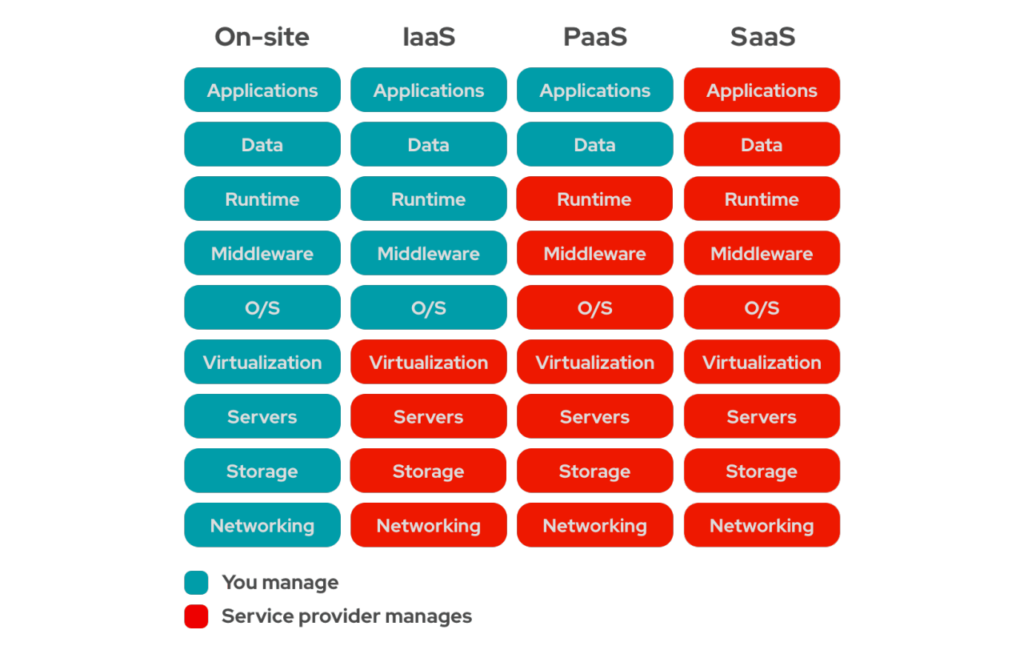
Despite more responsibility being shared with the cloud provider, it remains important to understand how this capacity of scale is achieved and how the infrastructure behind these services is organized. This is a concept that can vary from one provider to another in terms of naming or even organizing. Therefore, in this article, I will describe concepts that are similar to the approach adopted by three of the main providers in the market (Microsoft Azure, AWS and Google Cloud).
In terms of organization, the cloud provider organizes its infrastructure globally, divided into regions available in different countries and in accordance with local legislation within each country. Within each region, there is the organization of multiple datacenters that will ensure reliability and sufficient capacity to support demand at scale. Therefore, the regions are then divided into availability zones, which in turn are organizations of one or more autonomous and minimally distant datacenters (more than 100km) from the other zones to mitigate the effects of any potential physical or structural disasters.
For this entire structure, physical security in terms of access to these locations, hardware security and compliance with standards such as SOC,1, SOC 2, SOC 3, ISO 27001, etc., is guaranteed by the cloud provider. These audit reports are always available for access. But this model of responsibility is shared, and the customer must also ensure best practices in terms of architecture and the security of services being used in the cloud.
When it comes to structuring this cloud security from an architectural point of view, there is a wide range of approaches that vary according to the different possible architectures. There are, however, some concepts that are common to all approaches.
The first question is related to encryption. When structuring a cloud service architecture, there are accelerators and facilities to guarantee complete information encryption. This includes when information is at rest, which means data will always be encrypted when saved in the storage structures (either disk, block, object, or database storage). Equally, it includes when data is in transit, ensuring data is always traveling in an encrypted form (HTTPS, FTPS, SIPS, etc). It is important to emphasize that concern should not be focused solely on these protocols but should also extend to how data is managed internally, including the implementation of Mutual Transport Layer Security (mTLS) between microservices, encryption in communications with databases or encryption when interacting with the provider’s APIs, which will all greatly mitigate the impact of a possible security incident. Most of these functions and possibilities are native to cloud services, and it is the customer’s responsibility to be aware of these features and use cloud services as securely as possible.
A second very important point is in the management of audit logs. Public clouds provide high self-service capability and a very high level of automation. All of this is implemented through APIs, which is important to note because API usage logs are the most valuable asset for incident investigation and detection of possible threats, with every operation being reflected in these logs quickly. Therefore, working on security and threat detection in the cloud is directly linked to managing these logs and applying detection intelligence to them.
Finally, a well-designed landing zone (public cloud organization from the client perspective) in the cloud will support a correct architecture, which will offer efficiency and superior performance to applications taking advantage of cloud services, but will also ensure isolation and proper management of all audit logs. This includes feeding the Security Information and Event Management (SIEM) and Automated Thread Detection solutions, which will correlate events identified in the log for quick targeting or prevention of possible attacks. It will also support the Security Orchestration, Automation and Response (SOAR) solution in providing an automated response to incidents, which is a powerful tool for the Security Operation Center (SOC) and cloud engineering service to assertively engage with services delivered in the cloud.
Ultimately, fully realizing the capabilities of cloud services will involve making use of the correct expertise to ensure security is being worked on and architected from the initial stages, ensuring that the real value of detecting and responding to threats is realized.



















