The potential losses from a cyberattack are so vast, and the level of risk in today’s environment has increased so significantly, that a strong cybersecurity posture should now be considered a cornerstone of business success.
Any debate about whether cybersecurity is a smart investment for businesses is surely over. We have seen, and will continue to see, how the material damage caused by a single cyberattack could easily exceed a company’s funds set aside for cybersecurity. Being proactive is essential, because if you are just reacting, it will be too late.
While the scale of the potential danger is undeniable, evidence suggests that most businesses still have some work to do when it comes to preventing attacks. About 98% of the IT systems we’ve tested have had critical vulnerabilities. At the same time, 95% of the owners and IT directors of these companies believed that they did not have any major security problems in their infrastructure.
Cybersecurity Strategy and Skills
In this context, there are several key considerations for companies looking to invest wisely in cybersecurity solutions that can truly meet today’s challenges.
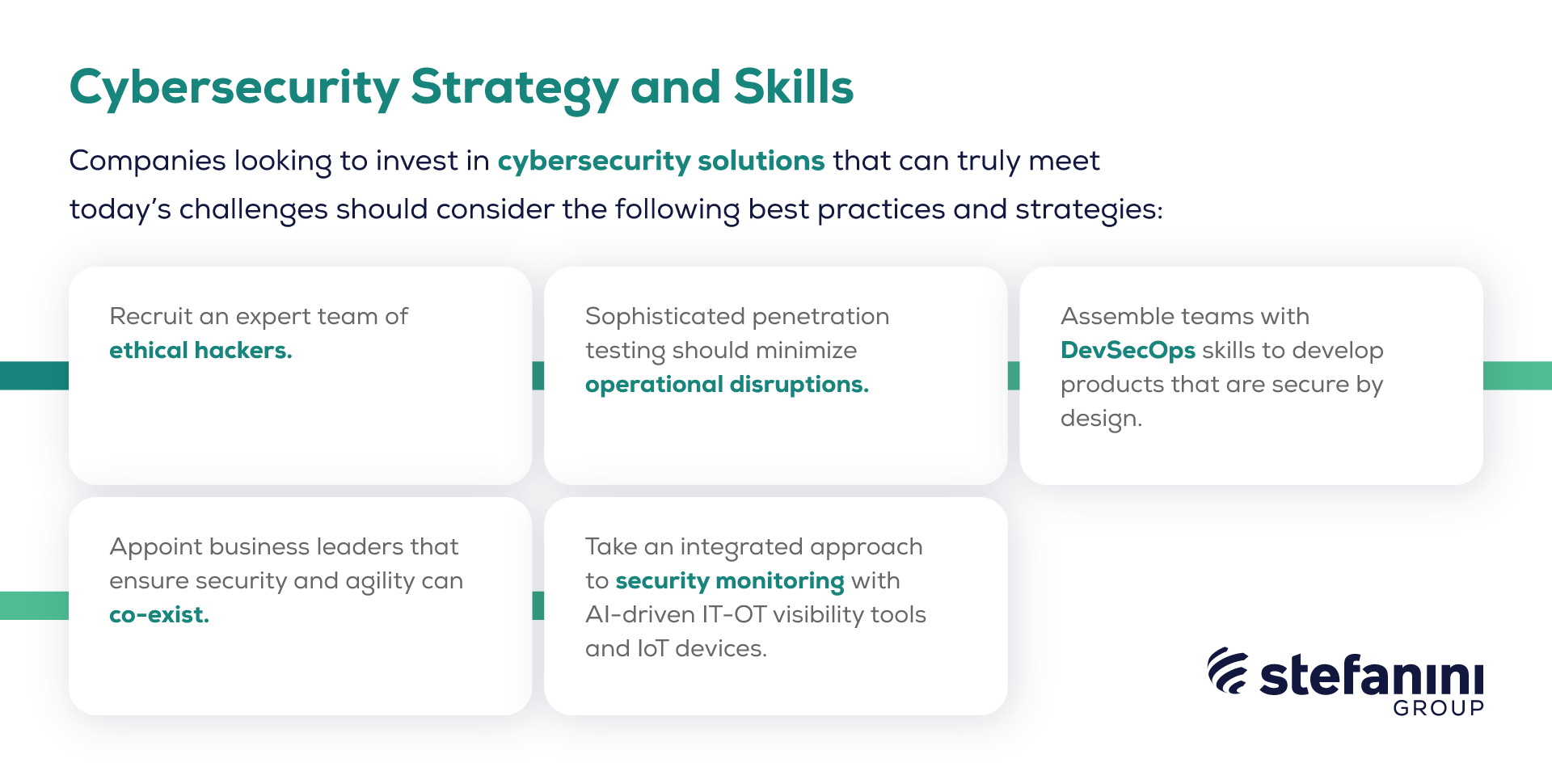
A solid security strategy is a necessary step to ensure that organizations do not introduce critical security gaps as they seek to benefit from new tech. Using the latest technological advances such as network monitoring and machine learning is important, but should always be accompanied by the best practices and key skills in Cybersecurity, such as the ones listed below:
- Human response to Hacking: Recruit an expert team of ethical hackers, who have a deep understanding of the mindset of cybercriminals looking to attack businesses.
- Minimal interruption of operations: Implement more sophisticated penetration tests to ensure tests have minimal impact on business operations.
- DevSecOps: Assemble teams with DevSecOps skills and make sophisticated use of automation to develop products that are secure by design.
- Best practices start at the top: Appoint the right business leaders, with the right skills, to the right roles so security and agility can co-exist.
- AI-driven operational technology visibility: Using operational technology (OT) visibility tools and connected IoT devices to take an integrated IT-OT approach to AI-driven security monitoring.
The technology exists to make this a reality. IDC predicts that due to advances in operational technology, by 2024, (OT) visibility tools will drive 66% of major industrial companies to adopt an integrated IT-OT approach to security monitoring.
“What unites businesses is that careful consideration of the right mix of skills, leadership, and best practices will be crucial to unlocking the full potential that Agile offers, while minimizing security risks.” Stéphane Olmanst, ICT Vice President of Stefanini Group.
The Top Skills Required for Cybersecurity Jobs
It goes without saying that a cybersecurity professional should have proficiency in programming languages, such as JavaScript, Python, C++ etc. to succeed in this role. However, there are other skills and abilities that are useful to a professional in cybersecurity as well. Here are a few of them.
Technical aptitude
As previously stated, a programmer must have technical skill and knowledge of programs to succeed. Beyond that, they should also understand scripting, controls and frameworks, operating systems (such as Windows, and MacOS) cloud tech, and even regulatory guidelines. Knowing this information is the first step to finding success as a cybersecurity technician.
Problem solving skills
In a cyberattack situation, oftentimes IT professionals have to think quickly on their feet to mitigate the situation. The difference of a few seconds in reaction time could result in potentially millions of user profiles compromised, or something equally disastrous.
In addition, most of cybersecurity is not reaction rather it’s being proactive, and anticipating where and how a potential attack could occur – which brings us to our next skill.
Understanding of hacking.
It’s like they say – “know thy enemy.” Knowing how a cyberattack might happen makes it much more likely that you’ll be able to prevent it, and safeguard against it. Oftentimes, professionals will employ something known as “ethical hacking” in which they will hack the system of a company to highlight vulnerabilities.
This allows them to quickly identify weak spots where security should be implemented, or increased. Think of it as a dress rehearsal of sorts- by testing it in a controlled manner, they find areas that may become problems in the future that could have been missed otherwise.
Attention to detail
This is a critical ability of a cybersecurity professional. The smallest oversight could leave a company’s system open to an attack. Cybercriminals are adept and finding and exploiting these overlooked areas to the detriment of the company.
They are trained and relentless in laying siege to a network, and a professional programmer has to be aware of this when implementing the measures to protect companies from these hackers.
Different Types of Cyberattacks
Part of having good cybersecurity is knowing what to look out for. Cyberattacks come in many different forms, and are often designed to trick users into allowing access to information. Here are a few of the most common types of cyberattacks.
Malware-based (Ransomware?)
“Malware” stands for “Malicious Software,” and refers to a type of software that will, once installed, hack your system for sensitive, otherwise protected information. A very common form of cyberattack, malware-based attacks come in many forms. A common type is ransomware, where hackers will demand the target pay a ransom in order to lift the virus from their computer.
Another is a Trojan attack- meaning specifically a Trojan Horse. This is where malware is hidden in otherwise legitimate appearing software- aka, an antivirus program.
Phishing Scams
When someone sends emails that appear to come from real sources in an attempt to steal information from a target, that’s known as a phishing scam or attack. It may come in the form of a link that takes the target to a website riddled with malware, or somehow trick the person into giving away sensitive information to the hackers- without knowing that they’re doing it.
These attacks are tricky, because often the victim doesn’t realize that they’ve been attacked at all- giving the hackers more time to target more people in the organization, and cause more damage.
Spear-Phishing and Whale-Phishing Attacks
Two subcategories of a phishing attack are known as spear phishing and whale phishing. Spear phishing is in reference to a more specifically targeted, personalized form of attack- where hackers will research a single target and employ methods like spoofing the “from:” line of an email to trick the target into thinking the message is personally relevant.
Whale phishing is when hackers target someone in the C-suite of a company- an executive with access to lots of sensitive information, and extra damaging if compromised.
MITM (Man in the Middle)
Think of MITM attacks as a form of spying. This attack is a breach in security where an attacker can then access and change data and messages sent back and forth between two parties. The trick here is that the parties don’t realize they’ve been compromised, and believe they are communicating as usual.
But the hacker could be not only stealing information, but changing the content of messages or data without either party knowing- which could lead to disastrous results, such as money, or information being sent to a different destination, and one party believing they were instructed to do so, by say a manager or co-worker.
DoS or DDoS (Denial of Service)
Not every form of cyberattack is to gain information- some are designed to shut down systems. In a denial-of-service attack, a system is sent multiple, fake service requests. Because of the strain this puts on the system’s resources, oftentimes sites are forced to shut down, or at the very least, they are unable to serve legitimate users as they normally would, causing processes to stall.
A side effect of this is that the system is often left vulnerable after shut down, leaving it open for further attacks.
Now that we’ve discussed some of the different forms of cyberattacks, let’s talk about some recent instances of cyberattacks on businesses, and the disastrous effects they’ve had.
No industry is safe from a cyberattack. Read this article about the top 5 cybersecurity threats facing the manufacturing industry and learn how to deal with them: https://stefanini.com/en/trends/news/top-5-manufacturing-cybersecurity-threats-how-to-face-them
Recent Examples of Cyberattacks
Toyota
Even a company as large as Toyota can still be susceptible to cyberattacks. In early 2022, three of their suppliers, Kojima, Denso, and Bridgestone, were targeted, causing Toyota to have to halt production at several plants around the world. These attacks caused a 5% decrease in output- which is a significant impact for a company of its size.
SpiceJet
Sometimes, merely an attempted cyberattack can have disastrous results. An Indian airline called SpiceJet was targeted earlier this year. Although the attack was mostly contained by the IT team, it still managed to do damage.
The attempted attack stranded hundreds of people at airports around the country, some having to wait upwards of six hours for restored information on their departing flights. When it comes to cybercrime- it’s not always just money and information that’s on the line, oftentimes, its people’s wellbeing that suffers.
Costa Rica Government
The government of Costa Rica has suffered from two major cyberattacks in 2022. Hacker group Conti first targeted the ministry of finance with a ransomware attack in early April, and demanded a $20 million dollar ransom to restore functionality. A second attack in May, linked to HIVE group, then focused on the healthcare sector.
These combined attacks caused Costa Rica to declare a state of emergency, the first time that cybercrime has provoked this, and proving that cyberattacks have the power to debilitate and destabilize entire governments, affecting millions of people in both government and private industries.
Conclusion
Organizations have been forced to rapidly accelerate their digitization initiatives, such as their work-from-home capabilities, while also embracing artificial intelligence (AI) to adapt supply chains and manufacturing processes. All of this has created a surge in cyberattacks targeting larger IT surfaces, with hackers trying to exploit noncompliant employee behaviors.
On top of this, the agile approach pioneered by tech companies is increasingly being adopted across the enterprise landscape, which, while accelerating time to market, potentially reduces your level of security diligence.
The good news is that with the right practices and the right mix of teams and skills, there doesn’t need to be tension between an agile approach and security. But make no mistake, finding the right team of professionals is an essential part of not just ensuring your business’ success, but keeping it as well- so hackers can’t steal it right out from under you.
Find Your Cybersecurity Solution at Stefanini!
The importance of strong cybersecurity can’t be overstated. Don’t leave yourself vulnerable for another moment! At Stefanini Group, our full range of cybersecurity services allows your company to invest in individual services that cover specific gaps in your current infrastructure- offering you tailored protection that’s just right for you! Speak with an expert today!
Ready to consult with a Stefanini expert? Enhance Cyber Defense Solutions with Stefanini
Stefanini is ready to bring the latest and best digital tools needed to optimize your operation.
Our team of experts will examine your processes and use their knowledge to find the technology that meets the unique concerns of any production line.
Ready to get started? Contact us today to speak with an expert!




















